Configuring Forms Authentication in SharePoint is a very popular topic in the SharePoint community. SharePoint Forms authentication allows you to store user membership, role, and profile information in a SQL Server database so that you don’t need to configure your users, groups, and profile properties in Active Directory. The following figure on MSDN web site will give you a good introduction on how it works.
Reference: http://msdn.microsoft.com/en-us/library/hh394901.aspx

Forms authentication was introduced in SharePoint 2007 and the process required manual configuration of the web.config files of central administration web site and the web application where you want to implement the forms authentication. IIS 7.X Management Console made it very easy to configure forms authentication with absolutely no need of modifying the web.config files directly. In this tutorial, you will learn to configure forms authentication for a SharePoint 2010 web application.
Convert Classic Mode Authentication to Claims Based Authentication
In SharePoint 2010, forms authentication doesn’t work in classic mode authentication which is the default mode of SharePoint 2007 and SharePoint 2010 based web applications. If you are upgrading to SharePoint 2010 from SharePoint 2007, you will have to convert your web application to claims based authentication after the upgrade to make forms authentication work. If you have created your web application in SharePoint 2010 using classic mode authentication, you still have to convert it to claims based authentication. This can be done easily using the SharePoint Management Shell.
NOTE: MAKE SURE TO BACKUP YOUR FARM BEFORE THE CONVERSION
- Start SharePoint 2010 Management Shell from Start –> All Programs –> Microsoft SharePoint 2010 Products.
- At the prompt type the following:
$WebAppName = "http:// yourWebAppUrl"$account = "yourDomain\yourUser"$wa = get-SPWebApplication $WebAppName
Set-SPwebApplication $wa -AuthenticationProvider (New-SPAuthenticationProvider) -Zone Default
- Your will receive a Migration prompt. Type “Yes”.
- Type the following commands to set a user as an administrator to the site.
$wa = get-SPWebApplication $WebAppName
$account = (New-SPClaimsPrincipal -identity $account -identitytype 1).ToEncodedString()
- The next step is to configure the user access policy for your web applications. Type the following commands:
$zp = $wa.ZonePolicies("Default")$p = $zp.Add($account,"PSPolicy")$fc=$wa.PolicyRoles.GetSpecialRole("FullControl")$p.PolicyRoleBindings.Add($fc)
$wa.Update()
- The web application will be updated in the previous step, it may take a while. After the update, you will need to type the following commands to migrate users from classic to claims based authentication in your web application.
$wa = get-SPWebApplication $WebAppName
$wa.MigrateUsers($true)
You may experience some issues after the migration. They are discussed at the Microsoft web site at http://technet.microsoft.com/en-us/library/gg251985.aspx.
Forms Authentication Setup Tasks
Following are the tasks that you need perform in order to setup forms authentication for your web application:
- Create a SQL Server membership database.
- Configure the SQL Server membership database permissions
- Configure connection string for the membership database in IIS 7.X
- Configure membership and role providers in IIS 7.X and create user accounts
- Create a new web application using claims based authentication
- Configure SharePoint Security Token Service (STS)
- Configure the Central Administration web site
- Configure People Picker section in web.config files
- Configure .NET Roles
- Test
TASK I – Create SQL Server Membership Database
The SQL Server Membership database stores membership, role, and profile information of your users. This database is created using Microsoft .NET Framework 2.0 aspnet_regsql command. Follow these steps to create this database on your database server.
- Logon to your SharePoint server using the user account that has permissions to create databases on your SQL Server. For this tutorial, I am using a test VM that we created in the SharePoint 2010 Single Server Farm Setup tutorial on my blog. I am logged on to my test VM using SharePoint\svc-spsetup account and password “ServiceAccount1”. This user account has been configured for dbcreator and securityadmin roles on my SQL server.
- Start command prompt as an administrator. This is done by right clicking on “Command Prompt” in the Windows Server start menu and selecting “Run as administrator” from the menu.
- Change your directory to Microsoft .NET Framework 2.X 64-bit directory which is located at C:\Windows\Microsoft.NET\Framework64\v2.0.50727 by default at the time of writing this tutorial.
Type aspnet_regsql and hit enter. - The ASP.NET SQL Server Setup Wizard will appear. Select “Next”. In the next screen “Configure SQL Server application services” option will be selected by default. Select “Next”.
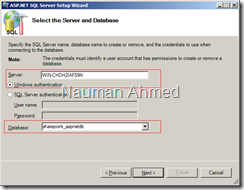
- In the next screen, specify the name of your server running the SQL server. Select “Windows authentication” and type “sharepoint_aspnetdb” in the “Database” option. Select “Next” in the subsequent screens to continue the database setup process. A screen titled “The database has been created or modified” will appear. Select “Finish” to close the wizard. Close the command prompt and go to SQL Server Management Studio. You should see “sharepoint_aspnetdb” in the list of databases.
TASK II – Configure SQL Server Membership Database Permissions
After creating the membership database, you will need to configure permissions for your SharePoint Application pool account. Follow these steps to configure permissions in the membership database for the SharePoint application pool account. In my test VM, my SharePoint web applications are using SharePoint\svc-spfarm AD user account for their application pool.
- In SQL Server Management studio, expand “sharepoint_aspnetdb” database node. Expand the security node to see the list of users. Right click on the “Security” node and select “New User” from the menu.
- In the “Database User" – New” window, specify the following:
User name: svc-spfarm
Login name: sharepoint\svc-spfarm
Owned schema: dbowner
Role Members: Select the following and select “OK”. You may need to scroll down in the list. Once the user is added, you will see it in the security node.
TASK III - Configure Connection String for the Membership Database in IIS 7.X
Now that we have our membership database setup, we need to configure connection string in IIS on the server level. Later on we will use this connection string in our web applications when configuring forms authentication. Follow these steps to add a connection string in IIS for our membership database:
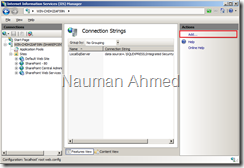
- Start Internet Information Service (IIS) Manager from Administrative Tools of Windows Server Start menu. Select the server name and from the “Features View”, double click on “Connection Strings”.
- Select “Add” from the “Actions” pane. On the “Add Connection String” screen, specify the following:
Name: SP2010ConnectionString
Server: localhost
Database: sharepoint_aspnetdb
Credentials: Use Windows Integrated Security
Select “OK” on the screen.
TASK IV - Configure Membership and Role Providers in IIS 7.X and Create User Accounts
Now that we have our connection string setup, we will configure the Membership and Role provider on the server level. The membership provider and role providers are features of Microsoft .NET Framework. The membership provider stores and manages the user information. The role provider stores and manages roles or groups. Follow these steps to configure these providers in IIS.
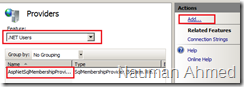
- In IIS Manager, select your server name from the left pane. Double click on “Providers”.
- In the “Providers” screen, you will see “.NET Roles” being selected in “Features” option. Two roles titled “AspNetSqlRoleProvider” and “AspNetWindowsTokenRoleProvider” exists by default. Select “Add” from the actions pane to add a new role provider. You may need to wait a while until the “Add Provider” screen appears. When you see the screen, specify the following:
Type: SqlRoleProvider
Name: SP2010RoleProvider
ConnectionStringName: SP2010ConnectionString
Application Name: /
Description: SQL Role Provider for SharePoint 2010 Forms authentication
Select “OK” to create the role provider. - From “Features”, select “.NET Users”. “AspNetSqlMembershipProvider” is added by default. Select “Add” to add a new membership provider. In the “Add Provider” screen, specify the following:
Type: SqlMembershipProvider
Name: SP2010SQLMembershipProvider
Profile Properties:
EnablePasswordReset: True
EnablePasswordRetrieval: True
RequireQuestionAndAnswer: True (This is required for password retrieval)
Data:
ConnectionStringName: SP2010ConnectionString
General:
Application Name: /
Description: SQL Membership Provider for SharePoint 2010 Forms authentication
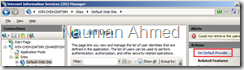
Select “OK”. - Now that my connection string, role, and membership provider are set on the server level, I can test the integration. A default IIS site is created when IIS configured. Select “Default Web Site” in IIS Manager.
Double click “Connection Strings” in the features to display connection string. Select “LocalSqlServer” connection string and select “Remove” from “Actions” pane to remove it. - Now that the default connection string is deleted, we have to update the “Default Web Site” settings to use our new connection string and providers. Select the “Default Web Site” again. Double click “.NET Users” from the “Features” pane. You will get an error. Select “OK”.
In the “Actions” pane, select “Set Default Provider…”.
Select “SP2010SQLMembershipProvider” from the “Default Provider” drop-down.
Select “OK”.
Select “Providers” from the “Related Features” section.
Select “AspNetSqlMembershipProvider” and select “Remove” from the “Actions” pane. - We have to enable forms authentication next for the default web site. In IIS Manager, select the “Default Web Site”. Double click on “Authentication” from the “Features” pane in “IIS” section.
Select “Forms Authentication” from the list and select “Enable” from the “Actions” pane. - Go back to the “.NET Users” feature of “Default Web Site” in IIS. This time, you will see that the “Add” option in the “Actions” pane is enabled.
Let’s add a user. Select “Add” in the “Actions” pane. The “Add .Net User” screen will appear. Specify the following information.
User Name: spadmin
E-mail: spadmin@mywebsite.com
Password: FBAPass1?
Confirm Password: FBAPass1? <You need to specify a special character under default settings. You can change that in the provider settings>
Question: Who created SharePoint? <You can add your own question>
Answer: Microsoft
Select OK to add the user. You will notice that our test account is created!
Create another user with the following information:
User Name: fbareader
E-mail: fbareader@mywebsite.com
For rest of the option, use the values from previous step.
TASK V – Create a New Web application Using Claims Based Authentication
Now that we have tested our membership database setup and created a user, it’s time to have some fun in SharePoint. We are going to create a new web application with claims based authentication in central administration.
Note: If you have an existing web application that is using classic mode authentication, convert it to claims based authentication.
- Go to the Central Administration web site. Create a new web application with the following settings.
Authentication: Claims Based Authentication
IIS Web Site: Create a new IIS web site
Name: SharePoint FBA Web Application
Allow Anonymous: No
Claims Authentication Types:
Enable Windows Authentication: Checked
Integrated Windows Authentication: NTLM
Enable Forms Based Authentication: Checked
ASP.NET Membership provider name: SP2010SQLMembershipProvider
ASP.NET Role manager name: SP2010RoleProvider
Sign In Page URL: Default Sign In Page
Public URL: http://sharepoint:7800
Application Pool:
Create a new application pool: Selected
Application Pool Name: SharePoint FBA Pool – 7800
Configurable: SHAREPOINT\svc-spfarm
Database Server: <Default Selected>
Database Name: SharePoint FBA Pool – 7800
Database Authentication: Windows authentication
Leave all the default selected options as-is and selected OK to create the web application.
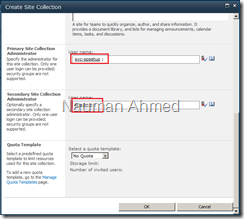
Select “Create Site Collection” link and let’s create a default site collection for this web application with the following settings.
Title: FBA SharePoint Web Application
Web Site Address: http://sharepoint:7800/
Template: Team Site
Primary Site Collection Administrator: SharePoint\svc-spsetup
Secondary Site Collection Administrator: spadmin <This is the forms authentication user>
Select “OK” to create the site collection. Wait until the site collection is created. - Click on the site collection link in the conformation screen. You will see the sign-in page with that allows you to sign-in with Windows or Forms Authentication. Our forms authentication setup is not yet complete. To make sure that the site working with Windows authentication, select “Windows Authentication” . It may take a while for the site collection to load for the first time so be patient! If you receive a SharePoint error, refresh the page and you should see the homepage this time. Notice that you are logged on with Windows user account.
TASK VI – Configure SharePoint Security Token Service (STS)
STS handles requests to manage, and validate security tokens. Security tokens are part of claims based authentication that stores information about users such as name, role etc. To read more on STS, you can go to http://technet.microsoft.com/en-us/library/ee806864.aspx. In this task we will configure the security token service to use the membership provider that we created.
Note: Sometimes, STS configuration can be tricky. I recommend adding the following element to STS web.config at C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\14\WebServices\SecurityToken file so that you know the nature of the error if something fails.
<serviceDebug includeExceptionDetailInFaults="false" />
<serviceBehaviors>
<behavior name="SecurityTokenServiceBehavior"><!-- The serviceMetadata behavior allows one to enable metadata (endpoints, bindings, services) publishing.
This configuration enables publishing of such data over HTTP GET.
This does not include metadata about the STS itself such as Claim Types, Keys and other elements to establish a trust.-->
<serviceMetadata httpGetEnabled="true" /><!-- Default WCF throttling limits are too low -->
<serviceThrottling maxConcurrentCalls="65536" maxConcurrentSessions="65536" maxConcurrentInstances="65536" />
<serviceDebug includeExceptionDetailInFaults="true" /></behavior>
</serviceBehaviors>
- Open IIS Manager and expand “SharePoint Web Services”. Select “Security Token Service Application”. Double click on “Connection Strings”.
- Select “LocalSqlServer” from the list and select “Remove” from the “Actions” pane.
- Following the steps in Task IV, add the AspNetSqlRoleProvider and AspNetSqlMembershipProviude. Do not delete any of the existing providers.
Feature: .NET Roles
Type: SQLRoleProvider
Name: SP2010RoleProvider
ConnectionStringName: SP2010ConnectionString
Application Name: /
Feature: .NET Users
Type: SqlMembershipProvider
Name: SP2010SQLMembershipProvider <Should be identical
ConnectionStringName: SP2010ConnectionString
Application Name: /
TASK VII – Configure Central Administration Web Site
At this point, the central administration knows about forms authentication and you don’t have to change anything. However, it is recommended that you change the default membership provider. Follow these steps to change the default membership provider to the membership provider we created earlier.
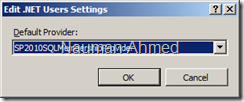
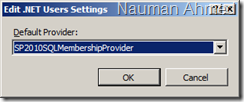
- Open IIS and select “SharePoint Central Administration v4” web site. Double click on “.NET Users”. This will take a while to load because the default membership and role provider doesn’t know anything about our sharepoint_aspnetdb database and you will get an error message. Select “Set Default Provider” from the “Actions” pane.
In the “Edit .NET Users Settings”, change the default provider to “SP2010SQLMembershipProvider”.
Select “OK”. - If everything goes fine, you will see the list of users.
- Open the Central Administration site in browser to make sure that it is working fine.
Task VIII - Configure People Picker section in web.config
The People Picker control is used to find and select users, groups, and claims when a site, list, or library owner assigns permissions in Microsoft SharePoint Server 2010. To learn more about PeoplePicker, go to http://technet.microsoft.com/en-us/library/gg602075.aspx. We need to include our membership and role provider information in web.config of Central Administration and SharePoint FBA Web Application web sites next. Follow these steps:
- In Windows Explorer, go to the central administration directory. By default it is created at C:\inetpub\wwwroot\wss\VirtualDirectories. On my test server, the central administration site was created in C:\inetpub\wwwroot\wss\VirtualDirectories\13350 folder.
- Make a copy of web.config file.
- Open web.config and search for <PeoplePickerWildcards>.
Copy <add key="AspNetSqlMembershipProvider" value="%" /> and paste it twice under the <add node.
Change the AspNetSqlMembershipProvider to SP2010SQLMembershipProvider.
Go to the next line and change AspNetSqlMembershipProvider to SP2010RoleProvider. - Close the file and open the site in the browser and make sure that it is accessible.
- Repeat the same process in the web.config of the web application we just created.
Task IX – Configure .NET Roles
.NET Roles works in the same way Groups work in Active Directory or SharePoint. Roles are disabled by default. In order to enable and manage roles, follow these steps:
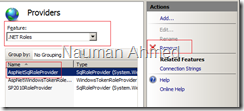
- In IIS Manager, select the “Default Web Site” and double click “Providers”.
Select “.NET Roles” in the “Feature” drop-down and delete “AspNetSqlRoleProvider” role. - In IIS Manager, select the “Default Web Site” and double click “.NET Roles” from the features.
Select “Enable” to enable roles.
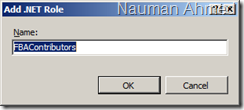
Select “Set Default Provider…” and select “SP2010RoleProvider” from the list. - Select “Add” to and add the following roles.
FBAContributors
FBAReaders - In IIS Manager, select the “Default Web Site” and double click “.NET Users” from the features. Double click on “fbareader” user. In the “Edit .NET User” setting, select “FBAReaders” checkbox and select OK.
- Login to the FBA site and go to Site Settings –> Site Permissions. Select “Grant Permission” option from the “Ribbon”.
Select the “Browse” icon in the next screen.
Type FBAReaders and hit enter in the find option.
Select FBAReaders and select “Add”.
Select “OK”.
In the “Grant Permission” option, select “Add users to a SharePoint Group” and select “FBA SharePoint Web Application Visitors [Read]” option.
Select OK.
Task X – Test
Looks like everything is all set. Open the browser and go to the web application URL that you just created. In my case, it exists at http://sharepoint:7800/.
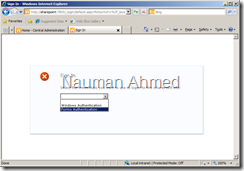
On the login page select “Forms Authentication”.
In order to sign in , use the following credentials and select “Sign In”.
User Name: spadmin
Password: FBAPass1?
You should be able to logon to the site now. Notice the user name spadmin at the top right corner.
Go to Site Actions –> Site Permissions and add fbareader user to the Visitors group.
Sign out of the web application and sign in as fbareader. You should be able to login to the site as a reader.




































































Explained really well!
ReplyDelete--Jonathan